The Intune Managed Browser now supports Azure AD SSO and Conditional Access!
Howdy folks,
If you follow the blog, you know that Azure AD Conditional Access (CA) lets you easily secure access to Office 365 and all the other apps you use with Azure AD. It is our fastest growing feature ever and more than 23M users are now protected by conditional access policies! As it’s taken off, we’ve listened closely to your feedback about how we could improve Conditional Access and what you’d like to see next.
One of the features customers like you have requested the most is integration with the Intune Managed Browser. So today I am excited to announce two enhancements that are now in public preview:
- Intune Managed Browser SSO: Your employees can enjoy Single Sign-on across native clients (like Microsoft Outlook) and the Intune Managed Browser for all Azure AD-connected apps.
- Intune Managed Browser Conditional Access Support: You can now require employees to use the Intune Managed browser using application-based Conditional Access policies.
Read on for more details.
Single Sign-on to Azure AD-connected apps in the Intune Managed Browser
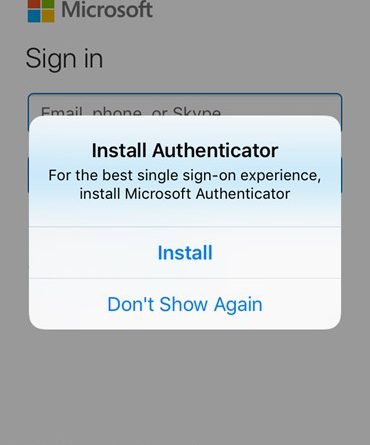
The Intune Managed Browser application on iOS and Android can now take advantage of SSO to all web apps (SaaS and on-premises) that are Azure AD-connected. When the Microsoft Authenticator app is present on iOS or the Intune Company Portal app on Android, users of the Intune Managed Browser will be able to access Azure AD-connected web apps without having to re-enter their credentials.
Let’s see how simple this is to have a better sign-in experience on iOS devices!
- Install the latest Intune Managed Browser. When using the app for the first time, you can take advantage of Single Sign-on by installing the Microsoft Authenticator app. Complete this step.

-
Sign-in, and navigate to any of your Azure AD-connected applications with Single Sign-on. You will be prompted to register your device to provide Single Sign-on to all applications. That’s it!
This capability expands on our previously announced integration between Azure AD Application Proxy and the Intune Managed Browser.

Pretty cool right?
Secure mobile browser access using Conditional Access and the Intune Managed Browser
You can also now restrict mobile browser access to Azure AD-connected web apps to the Intune Managed Browser only, blocking access from any other unprotected browsers like Safari or Chrome.
This allows you to secure access and prevent data leakage via unprotected browser applications. This protection can be applied to Office 365 services like Exchange Online and SharePoint Online, the Office portal, and even on-premises sites that you have exposed via the Azure AD Application Proxy.
To secure access, configure application-based Conditional Access policy in Azure AD and an App Protection policy for the Managed Browser in Intune.
Here’s how you do that:
Azure AD
It’s simple to create an Azure AD Conditional Access policy to lock down browser access to Intune Managed Browser. Learn how to setup an app-based conditional access policy on Azure AD. Here’s a screenshot of a policy targeting browser access.


Intune
Only a few more steps now! Create an Intune App Protection policy and target all users with for the Managed Browser application. Learn more on how to setup Intune App Protection policies here. A screenshot here shows how to target the managed browser application.

Your configuration is now ready! Users attempting to use unmanaged browsers such as Safari and Chrome will be prompted to use the Intune Managed Browser. If this is the first time, users will be prompted to install the Microsoft Authenticator on iOS or the Intune Company Portal on Android. Here is a screenshot of a blocked access when using Safari on iOS.

I hope you’ll give these new enhancements are try today. Here’s a set of quick links to get you started:
Quick Links
- How to use Azure AD Application Proxy
- Authoring conditional access policy
- App-based conditional access technical documentation
- App protection policies in Intune
- Configure Managed Browser policies in Intune
As always, we’d love to hear any feedback or suggestions you have. Just go here and let us know what you think!
Best regards,
Alex Simons (Twitter: @Alex_A_Simons)
Directory of Program Management
Microsoft Identity Division
Source: EM+S Blog Feed