This is SO cool! Use Azure AD to login to Azure Linux virtual machines
Howdy folks!
Linux virtual machines are very popular in Azure. A challenge everyone faces is securely managing the accounts and credentials used to login to these VMs. Typically, people create local administrator accounts and use either SSH keys or passwords to login to the VM. As people join or leave teams, new local accounts need to be created or old ones removed from these VMs. Managing who has access to a given VM is hard and admins need to periodically remove unnecessary SSH public keys or reset administrator passwords to protect against unauthorized access. To make things simple people often follow the risky practice of sharing admin account passwords among big groups of people. This makes it very hard to protect your production Linux VMs and collaborate with your team when using shared Linux VMs.
At the Build conference a few weeks back, we announced the public preview of a cool new Azure AD capability to make it easier to securely manage Azure Linux VMs. Using Azure AD login for Linux VMs, you can
- Login to your Azure Linux VMs using your Azure AD credentials. Basically, you can login to a VM using the same account you use to sign in to the Azure portal!
- Revoke access to Azure Linux VMs when employees leave your organization by disabling their account in Azure AD.
- Require multiple factor authentication (MFA) for login to Azure Linux VMs.
- Centrally control access to Azure Linux VMs using Azure Role Based Access Control (RBAC). You can make role assignments to grant regular user privileges or root (admin) user privileges when logging into Azure Linux VMs.
- If you have Azure AD Premium, you can also use Azure AD Privileged Identity Management (PIM) to configure just-in-time, time-bound access to Linux VMs.
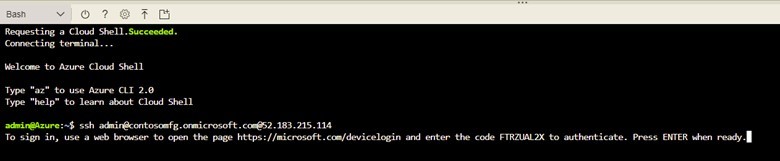
Let’s look at the login experience. After you enable Azure AD authentication, you can connect to the VM using your favorite SSH client and specify the UPN of your Azure AD account.

A one-time use code and a URL to login are displayed by the virtual machine. Enter the code on the Azure AD device authentication page (https://microsoft.com/devicelogin) to sign in.

If you’re already signed into the Azure portal or Office 365, you will not be prompted for credentials. If you have configured a policy to require MFA to login to Azure Linux VMs, you will be prompted to perform MFA.
Once you are logged in, return to the SSH client and hit Enter. You will be logged into the VM!

If your user account has been assigned the ‘Virtual Machine Administrator Login’ role, you will be able to escalate to ‘root’ user privileges using the ‘sudo’ command.
Want to try it out for yourself?
We are working to enable you to login to Windows Server VMs in Azure using Azure AD and expect to have it in preview later this year.
As always, we’d love to receive any feedback or suggestions you have! Head over to our Azure AD feedback forum or share comments on this blog post.
Best Regards,
Alex Simons (Twitter: @Alex_A_Simons)
Director of Program Management
Microsoft Identity Division
Source: EM+S Blog Feed