Presenting the new IIC Security Maturity Model for IoT
Organizations deploying IoT solutions often ask similar questions as they address security—What is the risk my organization takes on as we adopt IoT? How much security do we need for our scenario? Where should we invest for the biggest impact? To answer those questions, Microsoft co-authored and edited the Industrial Internet Consortium (IIC) IoT Security Maturity Model (SMM) Practitioner’s Guide. The SMM leads organizations as they assess the security maturity state of their current organization or system, and as they set the target level of security maturity required for their IoT deployment. Once organizations set their target maturity, the SMM gives them an actionable roadmap that guides them from lower levels of security maturity to the state required for their deployment.
Because not all IoT scenarios require the same level of security maturity, the goal of the SMM is to allow organizations to meet their scenario needs without over-investing in security mechanisms. For example, a manufacturing or an oil and gas solution involving safety needs an especially high maturity state.
The SMM complements Microsoft’s body of existing research and standards for IoT security, such as the “Seven Properties of Highly Secure Devices.” While the research in the Seven Properties paper provides a comprehensive deep dive into device security, the SMM takes a broader view of IoT security. This comprehensive model is used in the IoT security space to assess the maturity of organizations’ systems including governance/process, technology, and system security management. Other models typically address IT but not IoT, or IoT but not security, or security but not IoT. The SMM covers all these aspects and leverages other models where appropriate.
Applying the SMM to your organization
While the SMM’s intended audience is owners of IoT systems, decision makers, and security leaders, we expect assessment companies, and assessments groups within organizations, to be the main practitioners of the model. The SMM allows decision makers and security leaders to understand and consistently apply assessments performed by different groups. It also provides flexibility for industry extensions (currently being explored with several industry groups and associations) and allows for different types of visualization of the model results.
The SMM is organized as a hierarchy and includes domains, subdomains, and practices. This hierarchical approach enables the maturity and gap analysis to be viewed at different levels of detail, making it easier for organizations to prioritize gaps.
The SMM also makes an important distinction between security levels and security maturity states, helping organizations to understand the differences between what their goals need to be and where they are in their security journey. In the SMM, a security level is a measure of how much security you have. The SMM does not dictate what the appropriate security level should be for your organization. Rather, it provides guidance and structure so organizations can identify considerations for different security maturity states appropriate for their industry and systems.
Security maturity, on the other hand, is a measure of how well your security technology, processes, and operations meet your organization’s specific needs. The SMM helps you determine how much security you need, based on cost, benefit, and risk. The model allows you to consider various factors such as the specific threats to your organization's industry vertical, regulatory, and compliance requirements, the unique risks present in the environments your IoT operates in, and your organization's threat profile.
As you begin working with the SMM, it guides you through each step of the assessment using the model. Your organization begins by establishing a target state or identifying a relevant industry profile you want to target. Your organization then conducts an assessment to capture a current maturity state. By comparing the target and current states, organizations identify gaps. Based on the gap analysis, business and technical stakeholders can establish a roadmap, take action, and measure the progress. Organizations improve their security state by making continued security assessments and improvements over time. No matter how far along you are with IoT security, the model will help you close gaps that bring you to your desired security maturity.
Assessing security details with the security maturity model
Once you begin working with the SMM, it guides you through a rigorous approach to defining how well your security state meets your needs. To help you identify actionable areas to improve and to avoid blind spots in your plan, the SMM introduces domains, subdomains, and practices. You can gauge how well your organization is doing in each domain, subdomain, and practice along two dimensions — comprehensiveness and scope. Comprehensiveness is a measure of the depth and with higher levels indicating higher degree of maturity of a process or technology. Scope allows for identifying general, industry, and system specific requirements, ensuring the SMM can be tailored to your industry and use case with more precision than previous models could achieve.
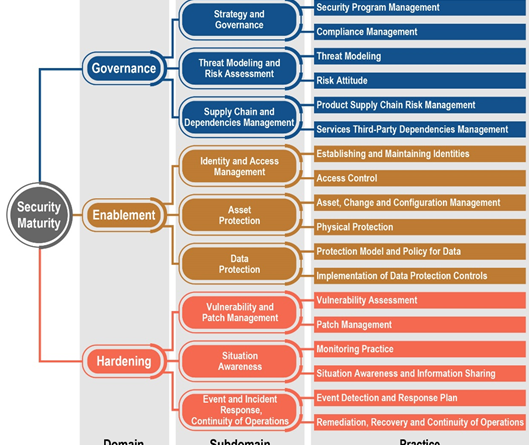
SMM Hierarchy
The domains in the SMM include governance, enablement, and hardening. These domains determine the priorities of security maturity enhancements at the strategic level.
- Governance influences business process and includes program management, risk management, and supply chain and third-party management.
- Enablement covers architecture considerations and security technology mechanisms and includes identity management, access control, and physical protection.
- Hardening defines countermeasures to deal with incidents and includes monitoring, events detection, and remediation.
The subdomains reflect the means of obtaining the priorities at the planning level. The practices define typical activities associated with subdomains identified at the tactical level.
The SMM includes practice tables grouped by domains and subdomains. Each SMM practice includes a table describing what must be done to reach a given comprehensiveness level at the general scope. For each comprehensiveness level, the table describes the objective and general considerations, a description of the level, practices that should be in place to achieve that level, and indicators of accomplishment to help assessors determine if the organization has met the requirements of the level.
Of course, general guidelines are often difficult to apply to specific scenarios. For that reason, an example follows each table using various industry use cases to demonstrate how an organization might use the table to pick a target state or to evaluate a current state. The guide also contains three case studies that show IoT stakeholders how to apply the process. The case studies include a smarter data-driven bottling line, an automotive gateway supporting Over the Air (OTA) updates, and consumer residential settings using security cameras. As our work on the SMM continues, we will work with industry organizations and associations to define industry profiles for the SMM.
Getting started with the SMM
If you want more information on exactly how the SMM works or how you can begin, the best spot to start is with the model itself: evaluate or improve your IoT security with the SMM today. To learn more about the SMM from its authors, watch our SMM introduction webinar.
For details on building your secure IoT solution on the trusted Azure IoT cloud services, see our Azure IoT Security Architecture for more information or start your free trial to get immediate hands on experience.
Source: IoT