Modern management and security principles driving our Microsoft Endpoint Manager vision
In this document I want to set forth Microsoft’s vision for how IT organizations will deliver, manage and secure this Modern Workplace going forward across all devices – with an emphasis on the definition and path to modern management of Windows PCs as organizations generally have well-managed PCs solution in place (usually built on ConfigMgr). This document was written for the IT teams responsible for delivering the Modern Workplace to their organizations to understand the Microsoft 365 vision and strategy for empowering them to delight their users, enabling them to work how, when and where they want, all while ensuring the organization’s data is safe and secure.
We live and work in a time in which there is more change happening at a more rapid pace than ever before. This is even more true in technology as the cloud and capabilities in machine learning and artificial intelligence are enabling organizations to learn and innovate faster than ever before. This is coupled with increasing expectations and needs of the users to be more connected, more aware, more productive, with more freedom to achieve in the ways that best enable and empower them. The way in which organizations empower employees across all the devices their users use is changing rapidly as they deliver work experiences that are more empowering and transformative for their users. Organizations desire to move to a consistent and unified way of enabling their users across all their devices and are looking for guidance on the best way to do this that is both empowering and secure. This is often referred to as modern management. At the core of modern management is cloud intelligence that empowers IT to transform the Modern Workplace to one that is “loved by users, loved by IT, and trusted by all.
Key Trends
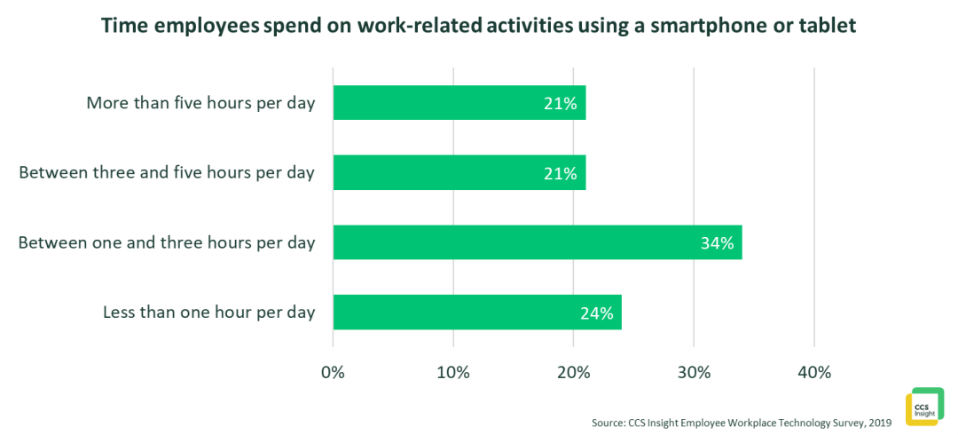
Mobility. More and more work is being done on mobile devices – phones, tablets and PCs. End-user research from CCS Insights shows 42% of employees spend more than three hours a day working on a mobile device. That number is 51% for Millennials born between 1990 and 2001. But ‘mobility’ is not just about mobile devices like smartphones and tablets. Organizations are more distributed than ever; users work from anywhere and everywhere on all their devices and expect their experience to be equal to working from a traditional office. In short, the office is now everywhere. Most commercial users work across multiple devices each day (both large and small screens) and want an experience that is consistent, reliable, connected and simple across all devices. The move to mobile and the move to cloud apps are closely connected. Mobile devices require cloud apps and services to enable and empower users.
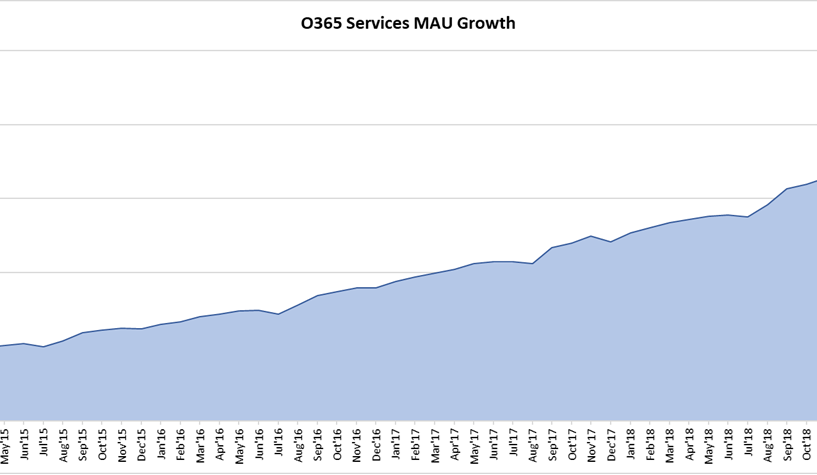
This chart shows the incredible usage acceleration of Office 365 – the most commonly used cloud business service; about every customer I meet with has or is in planning to move to Office 365. And over the last three years the number of mobile devices accessing the Office 365 services has tripled. Most organizations will have a mix of SaaS apps and local apps running behind the firewall that their users are required to use. In a world in which the perimeter-based security model is no longer effective and persistent threats and attacks are rapidly increasing in sophistication and impact, organizations must rethink their management and security strategies.
Increased Focus on the End-User Experience. Business leaders understand their employees work experience is a significant driver of employee sentiment, loyalty, and engagement. A truly Modern Workplace experience creates an image of a modern, forward-looking and innovation-driven organization to its employees that is continuously improving.
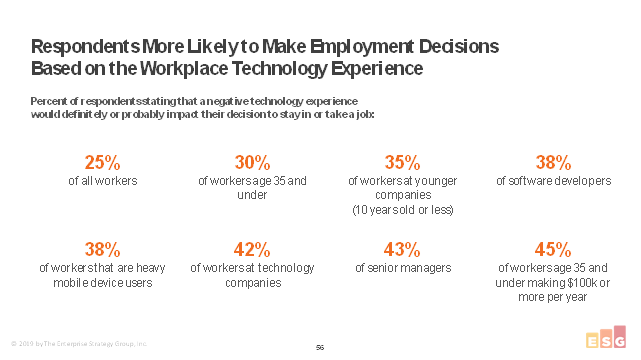
ESG is planning to publish end-user research that shows up 45% of employee make decision to take a job or stay with an organization on the quality of the work experience they are given at work.
Simplification. Organizations are recognizing that the complex environments they have deployed for managing and securing their organizations need to be massively simplified – both to deliver a better user experience and to increase their level of security. Especially in the face of increased sophistication in attacks, organizations see that simplicity is an architectural principle that brings with its increased security. Simple solutions have fewer moving parts to configure and worry about. A Modern Workplace is built on cloud intelligence that enables organizations to deploy security solutions such as Conditional Access (Zero Trust is an approach using Conditional Access) as cloud intelligence assists and automates the real-time evaluation of the users, devices and apps requesting access to ensure they are all trusted.
On the surface these three trends may not appear linked, but they are actually deeply connected. Simplification is one of the core things that drive improvements in the end-user experience. And as more cloud services are used by employees, the resulting cloud insights drive simplification.
Modern Management and Security Principles
Loved by users, Loved by IT, Trusted by Everyone. Core to modern management and security is delivering users the Modern Workplace that empowers them to achieve more across all their devices, while providing the required security and protection of the organization’s assets. Users love this experience because they can work where, when and how they want without reduction in functionality or experience. IT loves this experience because it provides a common and consistent method and tool to manage and enable users across all their devices, while also delivering the security and protection they require. Users and IT trust this solution because both the user’s privacy and the organization’s data and assets are secure.
Cloud intelligence with automated actions is the core. At the core of modern management and security is the use of cloud intelligence that is generated through learning across vast data sets. This cloud intelligence is applied through modern management to automate end-to-end actions, improve the end-user experience, and ensure devices are both secure and performant. Combining humans with cloud intelligence enhances the complementary strengths of both. Microsoft 365 brings together best-in-class productivity apps with intelligent cloud services to transform the way people work. With more than 900 million deployed Windows 10 PCs, 190 million commercial PCs, Macs, iOS and Android devices that are managed by ConfigMgr and Intune, 200 million Office 365 users, and more than 600 billion authentications serviced each month by Azure Active Directory (AAD), the cloud intelligence we can generate across these insights is powerful. Overall, there are more than seven trillion data points that come into Microsoft each and every day. Microsoft is uniquely positioned to: (a) learn from this incredible scale, (b) deliver insights and recommendations that are specific to each customer, and (c) help IT automate actions and proactively remediate issues. Through cloud intelligence, we can now automate complex tasks such as compatibility testing and identifying compromised user accounts. As the learning models operating on this data are refined and improved, they enable us to deliver insights that enable the Modern Workplace to continually improve as we apply what we learn across all of our Microsoft 365 customers.
Helps IT Prioritize Their Time and Efforts. Every IT leader and IT professional has a never-ending to-do list. One of their biggest challenges is knowing how to prioritize their time to have the largest impact on the business. Modern management and security applies cloud intelligence to first reduce the tasks IT has to do through automating common repetitive actions and second by taking automated actions. Modern management and security also provide IT with a customized list of actions that are prioritized based on the unique status of each organization and the impact to the business. These customized and prioritized actions are created by iterating on the right data sets to identify and learn what is happening in actual deployments around the globe and then guiding organizations on their next best actions – the actions that will have the greatest impact for their unique organizations based upon their unique deployments.
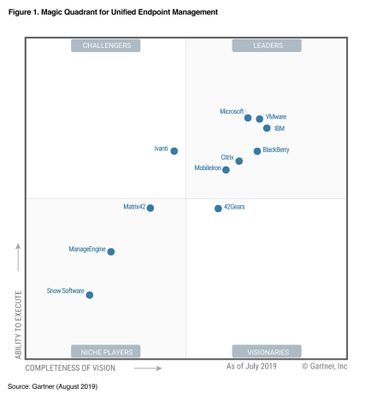
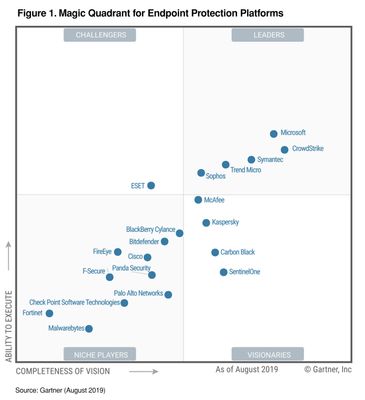
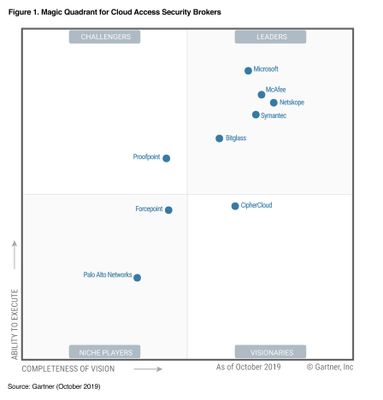
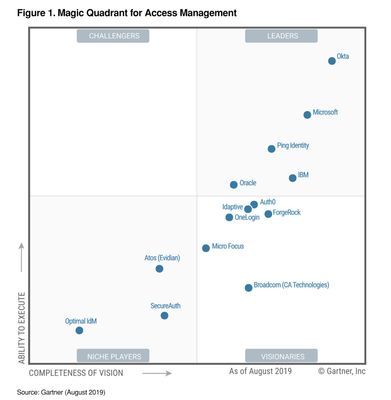
Connects IT and Security teams. Two big centers of gravity within customers who are responsible for delivering the Modern Workplace are the IT Operations (IT Ops) and the Security Operations (SecOps) teams. These teams need to work closely together as they define the requirements and then deploy/operate the Modern Workplace. The Security team is responsible for understanding the attacks/ risks/ breaches and ensuring the right policies, configurations and updates are in place. In most organizations the Security team defines these controls, and then the IT team translates those controls into policies that are implemented in the tools. Yet the reality is that these teams are not nearly as connected as they should be. From the security teams perspective, they may not always get the desired priority and response from IT. On the other hand, IT teams may sometimes feel security dictates prevent them from being most effective at their jobs. Modern management connects the IT and Security teams so that actions the security team requires are automatically communicated between the cloud services and implemented immediately, while the IT teams are able to automatically provide visibility back to security teams into actions and policies they have implemented. This enables seamless collaboration between the teams while honoring the roles and responsibilities. Microsoft’s Threat and Vulnerability Management solution identifies PCs that are open to known threats and vulnerabilities and automatically instructs Intune and ConfigMgr what to do to close the vulnerabilities. Microsoft has been identified as an industry leader by Gartner in all of the key technologies we believe to be critical to the success of a Modern Workplace: endpoint management, endpoint security, cloud access security, and identity. We believe Microsoft has a unique value here, with a better together story across management, security and identity, through a unified IT admin experience that brings these services together.
| 
|
| 
|
Continuously Improves the End-User Experience. One of the most precious assets organizations have is their people. People drive the innovation, differentiation and execution that power organizations to higher levels of productivity and value creation. The experience that IT delivers to their users has become a critical driver of not only productivity, but a driver of employee sentiment and company culture. Users are accustomed to the immediate on and immediate resume experiences on their phones. They want and deserve the same experience on their PCs. The reality that most commercial users experience on their PCs is not this today. The most common reasons for slow boot, slow resume, slow app launch and poor battery life are poor hardware (HDDs rather than SSDs for example) and the management and security agents that get loaded on commercial PCs. Organizations that apply the Microsoft 365 modern management stack are seeing boot times that are less than 30 seconds – down 85% from their previous configurations. Their PC resume times are as fast as their mobile phones. Battery life is double what they were before (increasing on average from 3.2 hours to over 7 hours). And these customers are seeing an average of an 85 percent reduction in the number of PC crashes. This is possible because they rely on what is built into Windows and driven through cloud intelligence. These improvements in the end-user experience delight users and drive significant a increase in employee sentiment.
Increases Security. As organizations modernize and use the Microsoft 365 native management and security capabilities, they see a significant increase in their security posture. The Modern Workplace that is built on Microsoft 365 puts the 7 trillion pieces of signal that come into Microsoft each day to work on your behalf. We learn at cloud scale, and when we see a new attack or a variation of an existing attack, that learning is instantly applied to all organizations using Microsoft 365. The Microsoft 365 services are also deeply integrated so our security analysis can be done at the intersection of identity, device, app, and service. Working at this intersection we can identity and then take action to protect and secure your organization – with the learnings of each customer, each device, each identity contributing to continuous security improvements for all customers, all while continually improving the end-user experience.
Enables IT and Service partners to Demonstrate and Prove Impact. As the IT and SecOps teams take advantage of these modern capabilities and practices that are built on cloud intelligence, they are able to demonstrate to the business the progress and the impact on their end-users. Modern management tracks the progress in areas such as end-user experience improvements and increased security and delivers simple to understand metrics and results that can be shared with business leaders and end-users. IT is core to the digital transformation of every organization, and the ability to clearly demonstrate the improvements and impact is critical to enabling the business (leaders and users) to understand their impact on business results. The Modern Workplace enables IT to take a “victory lap” as they demonstrate impact.
Empowers Partners. IT organizations look for rich and vibrant ecosystems that work together to empower them to deliver the Modern Workplace to their users. Platforms such as Microsoft 365 empower partners to add their unique value, and together the ecosystem delivers the comprehensive and complete solution that organizations require. These partners ecosystems are moving to the cloud and utilize cloud-based APIs to orchestrate end-to-end events across management and security. Microsoft 365 has one of the richest partner ecosystems across hardware, management, security, and productivity to empower IT to deliver, manage and secure the Modern Workplace. Through Microsoft Graph APIs, partners can integrate their unique value and insights into Microsoft 365, extending the capabilities and creating new business opportunities as they deliver new customer value. Our partners – OEM, management, security, virtualization, and more – all make Microsoft 365 more rich by integrating their unique capabilities.
Modernizing and Migrating at your own pace
Modern management does not mean cloud-only. It does not mean a migration away from ConfigMgr, or a migration to Intune. As stated earlier, modern management puts the cloud intelligence that comes from organizations like Microsoft to work to automate tasks, prioritize your efforts, connect the IT and Security teams, and continually improve the user experience. We do believe the destination many organizations will arrive at over time will be a cloud-only management solution with Intune and Microsoft 365 at the center, but we want to enable you to take advantage of our cloud capabilities incrementally at your own pace – without replacing infrastructure as some of you may not be ready for a full cloud migration. This enables you to get cloud value along with your on-prem deployments, on the road to full cloud/modern transformation.
We made a number of significant announcements this morning at Ignite. One big announcement was bringing together all of the Microsoft management solutions under a common brand – Microsoft Endpoint Manager. Microsoft Endpoint Manager is the single management solution to manage and empower your users across all of their devices. ConfigMgr, Intune, Desktop Analytics, Co-Management, Device Management Admin Console, … now are Microsoft Endpoint Manager. For many of you, your destination may be all-cloud. For many others of you, your destination may be ConfigMgr and Intune working together in co-management. Both are destinations and will be fully supported in the future.
The Microsoft Managed Desktop Service (MMD) Will Set the North Star for the Industry. The Microsoft Managed Desktop group is unique in that it is the only organization within Microsoft that has end-to-end responsibility for deploying, managing, and securing Microsoft 365 implementations for our customers. This team is unique in that it sits at this cross-section of identity, management, security, hardware and productivity and is chartered with delivering that end-to-end scenario for customers while driving changes and improvements across the entirety of Microsoft 365. Microsoft Managed Desktop is also unique in that it’s always learning at the intersection of these areas and then engineering new value that can only be delivered through this unique perspective.
If you want to understand our recommendations for deploying the Modern Workplace that is loved by users, loved by IT and trusted by all – Microsoft Managed Desktop is the reference, and I would encourage you to ask “what would Microsoft Managed Desktop do?” We will regularly publish aspects of the configuration, policies, and actions we take so you can compare what you are doing with Microsoft’s best practices and implement those same practices. The security baselines, metrics on boot, resume, crashes, etc. that we publish going forward will all be based on what we are seeing in our Microsoft Managed Desktop customers – who are running the Gold Standard configuration we are recommending for the industry.
How to Shift to Modern Management with Microsoft Endpoint Manager
Customers not using ConfigMgr. If you are one of the rare customers who is not using ConfigMgr to manage your Windows devices you should move straight to Microsoft Intune for management of all of your devices. It is highly likely that the solution you are currently using is not delivering modern management capabilities because they aren’t delivering the cloud insights that drive modern management. Even providers who classify themselves as Unified Endpoint Management (UEM) providers are not able to deliver these modern management capabilities because they do not have the unique data sets referenced above to learn from and deliver you the insights you need.
Customers using ConfigMgr and Intune together in Co-Management. This is the path that most customers will follow: The majority of Enterprise customers use ConfigMgr today for management of PCs, and many are now using Intune for managing their mobile devices. ConfigMgr customers rely deeply on ConfigMgr for updates, security, deployment and compliance actions for their PCs and server estates. The average ConfigMgr customers have made significant investments – on average, customers have more than 2,000 apps that ConfigMgr is deploying, managing, and updating across their estate. Organizations have made significant investments in the ConfigMgr OS deployment and imaging capabilities. Ensuring compatibility with this significant investment is critical. Perhaps most significant, most organizations’ security and compliance solutions for deploying updates to their PC estate are built on ConfigMgr. To start your shift to modern management and start to use cloud intelligence you simply need to attach Intune to your ConfigMgr deployment – we call this Intune tenant attach. The 1910 release of ConfigMgr will make it easy to create and attach an Intune tenant to your ConfigMgr deployment. You can start putting that cloud intelligence to work immediately without making a single change to your ConfigMgr policies. You get further cloud value when you register your ConfigMgr devices with Intune – we call this co-management. Co-management is a unique ConfigMgr and Intune set of capabilities in which the two are working together to bring cloud intelligence and automation to your PC estate. If you choose to move ConfigMgr workloads to Intune, you can do that one at a time – a low-risk approach that enables you to move at the pace that makes the most sense for your organization. Microsoft Endpoint Manager (ConfigMgr and Intune) work closely to ensure there are never conflicting policies set on your PCs. To get more details on co-management, please watch this video. We will continue to significantly invest in co-management to make the transition to a fully Cloud model more and more simple – such as migrating apps from ConfigMgr to Intune.
Customers Using ConfigMgr and Intune for Separate Device Cohorts. At Microsoft we started our move to modern management with co-management. We now want to move to 100 percent cloud. In this model you pick a date, and all new PCs provisioning or existing PCs that are re-provisioned are cloud-only. One of the nice benefits of this route is you can start with a clean slate on these devices. One of the things we encourage you to do is really look at is the Group Policies that have been configured in your organization over the past 20 years – chances are, you only need a fraction of what has been configured and being applied, and you’ll find new policies such as the Security Baselines that will greatly improve your threat posture. At Ignite we announced Policy Analytics, which will help you understand your Group Policies – what has been configured and what could be eliminated going forward. The base MDM layer in Windows 10 does not have all the functionality that is needed to service enterprise PCs, so we have extended that with an Intune agent. We have been able to take our experience from more than 20 years of managing PCs, with ConfigMgr managing more than 150 million PCs and apply that experience and code to deliver what is required to enable cloud-only management. As the PC fleet is replaced over time or PCs refitted (such given to a different employee), you provision them to be cloud only.
In both of the ConfigMgr uses cases, you should not think about ConfigMgr and Intune as separate offerings, but within the continuum of Microsoft Endpoint Manager.
Virtual and Distributed. The Modern Workplace uses a mix of distributed and virtualized applications and desktops to empower users – especially the Cloud PC. The Cloud PC is a full Windows 10 Desktop running in Azure using Windows Virtual Desktop and enables any users to access their full desktop from any device – managed/unmanaged or trusted/untrusted. The Modern Workplace can make real-time decisions on the best method to user to deliver on the user’s needs based on the trust of each request and each session. Windows Virtual Desktop is unique in that it is the only solution that enables multi-user Windows 10 deployments in the public cloud, is optimized for Office ProPlus apps, and has all of the management and security of Microsoft 365 built in. In the long run, the most common virtualization solution that will be used will be Windows Virtual Desktop.
Get started right away
Here’s a recap of the resources available to get started with this right away. I referenced many of these links during the article, as well
- Announcement of Microsoft Endpoint Manager
- Learn more about Microsoft Managed Desktops
- Quick-start videos to cloud attach your PC management
- Assess, Plan and Deploy with Microsoft FastTrack service
- Enterprise mobility customer stories
I am excited about the future. Cloud intelligence offers insights that are changing the future of management, and I am excited about the work we are doing to bring Microsoft Endpoint Manager and the value of co-management to you to help you simplify your world and help you deliver the Modern Workplace to your users!
Acknowledgements
Gartner, Magic Quadrant for Endpoint Protection Platforms, 20 August 2019, Peter Firstbrook, Dionisio Zumerle, Prateek Bhajanka, Lawrence Pingree, Paul Webber
Gartner, Magic Quadrant for Access Management, 12 August 2019, Michael Kelley, Abhyuday Data, Henrique Teixeira
Gartner, Magic Quadrant for Unified Endpoint Management Tools, 6 August 2019, Chris Silva, Manjunath Bhat, Rich Doheny, Rob Smith
Gartner, Magic Quadrant for Cloud Access Security Brokers, 22 October 2019, Steve Riley, Craig Lawson
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from [insert client name or reprint URL].
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Source: EM+S Blog Feed