Customize your secure VM session experience with native client support on Azure Bastion
This blog post has been co-authored by Isabelle Morris, Program Manager, Azure Networking
As organizations move their mission-critical workloads to the cloud, connecting to virtual machines (VMs) directly over the public internet is becoming more of a security risk. The more public IP addresses a customer has attached to VMs in their virtual network, the larger their attack surface becomes and the more vulnerable they are to security threats. The more secure alternative is to deploy a managed jumpbox service that reduces the number of public entry points to a customer’s resources in the cloud. The ideal managed jumpbox service should prioritize both security and flexibility to choose how you connect to your resources. Azure Bastion, Azure’s managed jumpbox service, now provides customers with the ability to customize their connection experience to use a native client of their choice.
Azure Bastion overview
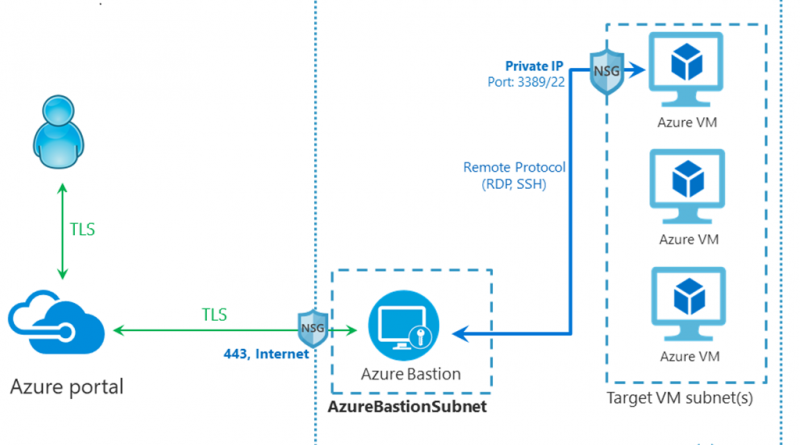
Azure Bastion is a fully managed jumpbox-as-a-service that provides secure and seamless Remote Desktop Protocol (RDP) and Secure Shell Protocol (SSH) access to your VMs in local or peered virtual networks. Azure Bastion provides connectivity directly from the Azure portal using Transport Layer Security (TLS). With Azure Bastion, your VMs do not need a public IP address, protecting your virtual machines from exposing RDP and SSH ports to threats on the public internet, while still providing secure access using RDP and SSH. With native client support available on the Standard SKU for Azure Bastion, you now unlock customizable features and added functionality in your VM sessions.
More flexibility to choose how you connect to your VMs
The primary way to connect to your VMs using Azure Bastion is through a quick and simple experience in the Azure portal. Users and administrators can navigate to their Azure VM in the portal and then open a web-based VM session using Azure Bastion. This experience eliminates the need to download any clients, agents, or configure files prior to accessing the VM.
Some customers value integration with existing and familiar processes. With the support for native clients on Azure Bastion, these customers can use command-line based access and a native client of their choice to reach their target VMs. This allows them to use Azure Bastion with a more accessible or familiar user interface, and to integrate connectivity to VMs via the service into their existing scripts.
Native client support offers three Azure CLI commands: az network bastion rdp, az network bastion ssh, and az network bastion tunnel. The az network bastion rdp command and az network bastion ssh enable connectivity to the target VM directly and use the clients mstsc and az ssh respectively. Meanwhile, the az network bastion tunnel command allows more flexibility by establishing a tunnel to the target VM on a specific port, and then allowing the user to connect to the VM using a custom client and the specified port.
Customers now can choose how they connect to their VMs via Azure Bastion—a simple, quick web-based experience or an integrated and customizable experience using a native client.
Simplify your login experience with Azure AD-based authentication
Azure Bastion native client support also unlocks an additional authentication option for users. With the az network bastion rdp and az network bastion ssh commands, users can use their Azure Active Directory (Azure AD) account to access their VMs. Using Azure AD for authentication provides enhanced identity security in conjunction with Azure Bastion’s existing networking security by eliminating the need to manage local VM credentials. For SSH, the Azure AD authentication also simplifies the connect experience by using the credentials the user has already provided to log into Azure CLI and taking them directly to their VM session.
File upload and download to a VM using a native client
Azure Bastion now supports file transfer between your target VM and local computer using Azure Bastion and a native RDP or SSH client. To both upload and download files, users must use the Windows native client on a Windows machine and the az network bastion rdp command. With RDP, users can easily transfer files between their target VM and local Windows machine in just a few clicks. For customers using non-Windows native clients or SSH, the az network bastion tunnel command supports file upload from your local computer to target VM. Third-party clients may also support file download for these scenarios.
Take advantage of native client support for your VM sessions
To learn more about native client support on Azure Bastion, refer to the Connect to a VM using a native client and Azure Bastion documentation. You can also follow our step-by-step guide on transferring files in the Upload or download files using a native client connection documentation.
Source: Azure Blog Feed