Azure Security Center adds support for custom security assessments
Azure Security Center monitors operating system (OS) configurations using a set of 150+ recommended rules for hardening the OS, including rules related to firewalls, auditing, password policies, and more. If a machine is found to have a vulnerable configuration, a security recommendation is generated. Today, we are pleased to preview a new feature that allows you to customize these rules and add additional rules to exactly match your desired Windows configurations.
The new custom security configurations are defined as part of the security policy, and allow you to:
- Enable and disable a specific rule.
- Change the desired setting for an existing rule (e.g. passwords should expire in 60 days instead of 30).
- Add a new rule based on the supported rule types including registry, audit policy, and security policy.
Note: OS Security Config customization is available for Security Center users in the Standard tier on subscription level only.
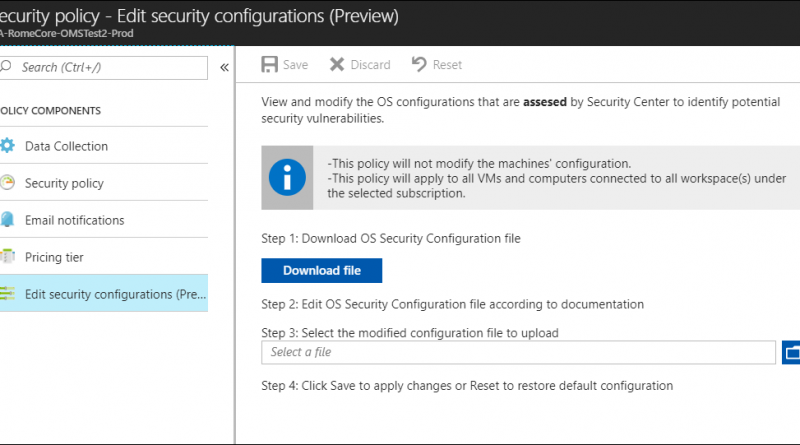
To get started, open Security Center, select Security policy, choose a subscription, and “Edit security configurations (preview)” as shown below.
In the “Edit Security Configurations rules” blade, you can download the configuration file (JSON format), edit the rules, upload the modified file, and save to apply your changes. The customized rule set will then be applied to all applicable resource groups and virtual machines during the next assessment (up to 24 hours).
To learn more about the new feature and file editing guidelines, please visit our documentation page.
Source: Azure Blog Feed