Announcing new capabilities in Azure Firewall
Today we are excited to launch two new key capabilities to Azure Firewall.
- Threat intelligence based filtering
- Service tags filtering
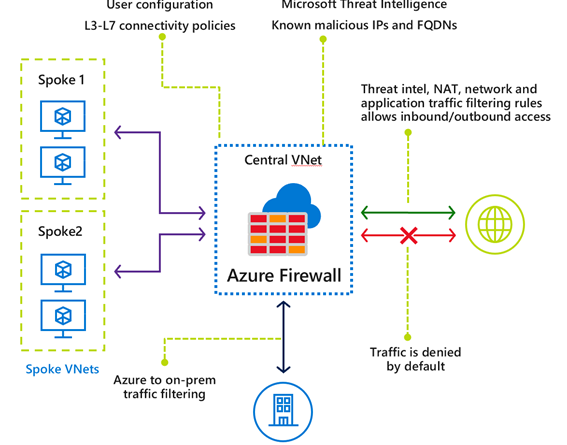
Azure Firewall is a cloud native firewall-as-a-service offering which enables customers to centrally govern all their traffic flows using a DevOps approach. The service supports both application (such as *.github.com), and network level filtering rules. It is highly available and auto scales as your traffic grows.
Threat intelligence based filtering (preview)
Microsoft has a rich signal of both internal threat intelligence data, as well as third party sourced data. Our vast team of data scientists and cybersecurity experts are constantly mining this data to create a high confidence list of known malicious IP addresses and domains. Azure firewall can now be configured to alert and deny traffic to and from known malicious IP addresses and domains in near real-time. The IP addresses and domains are sourced from the Microsoft Threat Intelligence feed. The Microsoft Intelligent Security Graph powers Microsoft Threat Intelligence and provides security in multiple Microsoft products and services, including Azure Security Center and Azure Sentinel.
Threat intelligence-based filtering is default-enabled in alert mode for all Azure Firewall deployments, providing logging of all matching indicators. Customers can adjust behavior to alert and deny.
Figure 1 – Azure Firewall concept architecture
Managing your firewall
Logging analysis of threat data and actionable insights are all crucial and central themes to planning, building, and operating applications and infrastructure.
Azure Firewall provides full integration with Azure Monitor. Logs can be sent to Log Analytics, Storage, and Event Hubs. Azure Log Analytics allows for the creation of rich dashboards and visualization. Along with custom data queries this powerful integration provides a common place for all your logging needs, with vast options to customize the way you consume your data. Customers can send data from Azure Monitor to SIEM systems such as Splunk, ArcSight and similar third party offerings.
Figure 2 – Azure Firewall detecting a compromised VM using threat intelligence and blocking these outbound connections
Figure 3 – Azure Firewall detecting port scan attempts using threat intelligence and blocking these inbound connections
Service tags filtering
Along with threat intelligent-based filtering, we are adding support for service tags which have also been a highly requested feature by our users. A service tag represents a group of IP address prefixes for specific Microsoft services such as SQL Azure, Azure Key Vault, and Azure Service Bus, to simplify network rule creation. Microsoft today supports service tagging for a rich set of Azure services which includes managing the address prefixes encompassed by the service tag, and automatically updating the service tag as addresses change. Azure Firewall service tags can be used in the network rules destination field. We will continue to add support for additional service tags over time.
Central management
Azure Firewall public REST APIs can be used by third party security policy management tools to provide a centralized management experience for Azure Firewalls, Network Security Groups, and network virtual appliances (NVAs). In September 2018, we announced the private preview for Barracuda’s new service, AlgoSec CloudFlow and Tufin. We are happy to announce that AlgoSec CloudFlow is now available as a public beta. Learn more and join at the Algosec website.
We want to thank all our customers for their amazing feedback since Azure Firewall became generally available in September 2018. We continue to be amazed by the adoption, interest, positive feedback, and the breadth of use cases customers are finding for our service. Please do keep your feedback coming and we look forward to continuing to advance the service to meet your needs.
Learn more
Source: Azure Blog Feed