Don’t build your cloud home on shaky foundations
You probably wouldn’t furnish a house you’re building with a state of the art entertainment system without first installing doors and an alarm system. Similarly, it isn’t advisable to put valuable applications and data used to run your business in the cloud without ensuring the proper foundational security and governance controls are in place.
Great buildings aren’t built on weak foundations
Many organizations struggle with how they want their cloud home to look, often so anxious to move that proper planning is ignored. Whether adopting PaaS, IaaS, or SaaS, properly planned governance and security foundations are key to ensuring a protected and controlled environment.
Building governance and security foundations in Azure
Before loading mission critical workloads or data, ensure your foundational governance model considers your organization’s operational, security, and compliance requirements without slowing down your adoption. Scale your business cloud footprint with peace of mind while leveraging the agility offered by cloud resources.
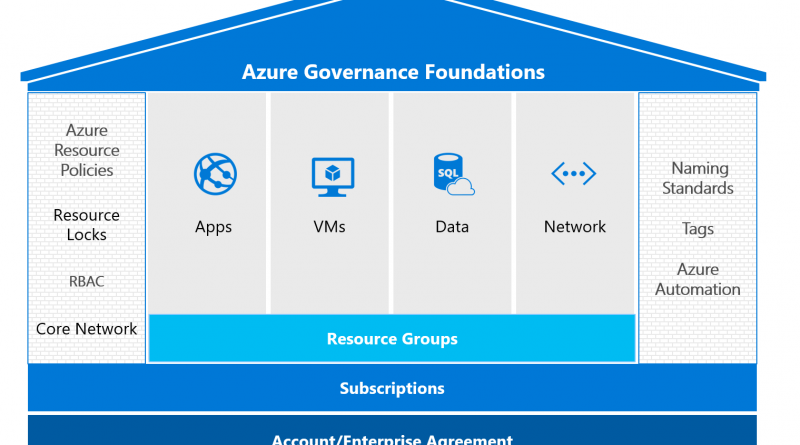
There are 6 top design considerations you should consider when laying the foundational components for a structured governance model in Azure:
1. Accounts/enterprise agreement: The cornerstone of governance allowing for subdivisions into departments, accounts, and subscriptions.
- Best practice: Use an O365 mailbox or on-premise monitored mailbox whose account is synchronized to O365 to automate assignment and revocation as part of your Identity and Access management policies.
2. Subscriptions: This is the administrative security boundary of Azure, containing all resources and defining several limits including number of cores and resources.
- Best practice: Design the organizational hierarchy, keeping in mind that one or multiple subscriptions can only be associated with one Azure AD at a time. Plan based on how your company operates, understanding the impact on billing, resource access, and complexity specific to your needs.
- Tip: Keep the subscription model simple but flexible enough that it can scale as required.
3. Naming standards: Cohesiveness is key for locating, managing, and securing resources while minimizing complexity. Leverage existing standards to use a similar naming scheme for resources.
- Best practice: Review and adopt the patterns and practices guidance to help decide on a meaningful naming standard, and consider using Azure Resource Manager policies to enforce them.
4. Resource policies and resource locks: Mitigate cost overruns, data residency, or accidental outages that can bring your organization down. Create a policy preventing compute resources to be created outside of Azure Canadian regions to ensure adherence to compliance policies mandated for certain types of data. Ensure specific types of VMs can be created to ensure budget adherence for dev test resource groups. For labeling, create a policy that enforces tagging to ensure production environment resources are tagged from dev/test resources at the time of creation.
- Tip: Leverage the use of resource locks to ensure certain key resources can’t be easily deleted.
5. Implement a least privileged access model: Permissions are inherited from the subscriptions to the resource groups and the resources within them including storage, network, and VMs.
- Best practice: Delegate access based on need and tasks. For example, cloud operators can be added to the Virtual Machine Contributor role for the resource groups they manage as opposed to subscription level. For additional security, also enforce Multi-Factor Authentication for access to resources by privileged accounts.
6. Implement Azure Security Center and Azure Advisor: Understand your current security posture by enabling Azure Advisor and Azure Security Center which will allow you to:
- Apply policy to ensure compliance with security standards.
- Find/fix vulnerabilities before they can be exploited across VMs, networks, and storage.
- Optimize your Azure resources for high availability, security, performance, and cost.
- Implement personalized recommendations with ease.
To learn more about Azure Governance, reference the Azure enterprise scaffold. Contact Microsoft Services to find out how we can help you implement a scalable and future-proof Azure governance framework.
Source: Azure Blog Feed