Announcing new Azure Security Center capabilities at RSA 2018
Migrating your workloads to the cloud can enable some inherent security benefits. With cloud scale machine learning and security analytics, you can mitigate threats quickly, making your environment more secure and your organization more productive.
Azure Security Center provides centralized visibility of the security state of your resources and uses the collective intelligence from machine learning and advanced analytics to not only detect threats quickly but to help you prevent them. It’s agent-based approach helps gain deeper security insights from the workloads and extends these protections to workloads running on-premises as well as other clouds, providing a unified security management for you.
Today we are excited to announce several capabilities in Azure Security Center that will provide enhanced protection to help you keep pace with the evolving cybersecurity landscape:
Visibility and governance at the organizational level
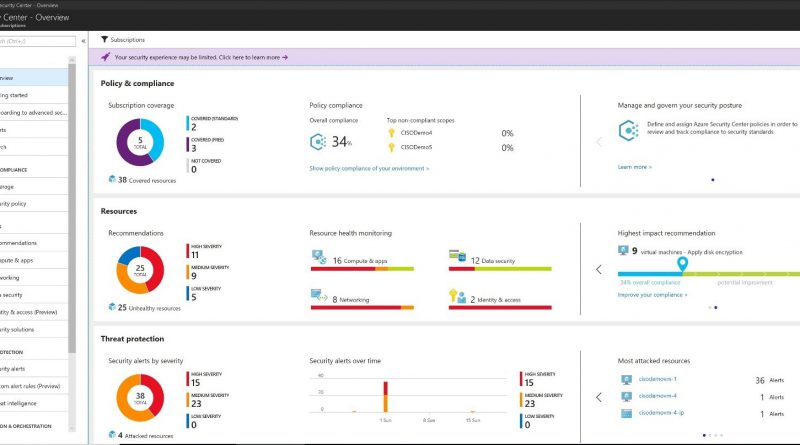
Take advantage of a new overview dashboard to gain visibility into your security state from an organizational level instead of a subscription level. To help organizations identify and address the challenges of managing an organization-wide security posture, you can now set security policies for management groups in your organization. You can also monitor it with an organization-wide compliance score as well as a breakdown score per subscription and management group.
Improve your productivity
Integrated security configuration in the Virtual Machine experience: Securing your resources in IaaS is important, which is why we’ve made it even simpler for you to do. As you create virtual machines in Azure, security configuration is now integrated into the virtual machine experience. In just a few clicks, you can enable Security Center and quickly assess the security state of your virtual machine, get actionable recommendations and mitigate risks.
An Identity & Access Management section will make it easier to discover if you have enabled access controls, such as multifactor authentication, for your applications and data. You can also discover identity and access issues and receive instructions for remediation.
Reduce your exposure to threats
Just-in-time VM access general availability: Previously in preview, the Just-in-Time VM access will be generally available today. It allows you to protect against threats such as brute force attacks by reducing access to virtual machine management ports only when it is needed.
Adaptive application controls: Using machine learning, Security Center recommends applications that should be whitelisted. Two new improvements will be available in preview today. First, you can get recommendations for new file types such as MSIs and scripts. Second, you can group virtual machines based on the similarity of applications running on them. Both of these enhancements are to improve the accuracy of the whitelisting policy that Security Center recommends for the virtual machines in a specific workload, and make it even easier for you to block unwanted applications and malware.
Interactive network security monitoring: Get visibility into the network components within your virtual networks in Azure from a new interactive topology. You can explore the connections between your virtual networks, subnets and nodes. You get actionable recommendations if vulnerabilities such as missing network security groups or web application firewalls are detected so you can take the appropriate next step.
File integrity monitoring (FIM): To help protect the integrity of your system and application software, Security Center is continuously monitoring the behavior of your registry and configuration files. If some abnormal change to the files or a malicious behavior is detected, Security Center will alert you so that you can continue to stay in control of your files.
Extending threat protection to containers: You can now get visibility into security posture of container environment and monitor for unsecure configuration on the container engine.
New secure configuration assessments for servers: A new web security configuration assessment helps you find vulnerabilities in your IIS web servers running on IaaS VMs and provides actionable recommendations to mitigate the risks.
Quickly detect and respond to threats
Integration with Windows Defender Advanced Threat Protection for servers (WDATP): Security Center now harnesses the power of WDATP to provide improved threat detection for Windows Servers. Microsoft’s vast threat intelligence enables WDATP to identify and notify you of attackers’ tools and techniques, so you can understand threats and respond. To uncover more information about a breach, you can explore the details in the interactive Investigation Path within Security Center blade. To get started, WDATP is automatically enabled for Azure and on-premises Windows Servers that have onboarded to Security Center.
Fileless Attack Detection: Security Center uses a variety of advanced memory forensic techniques to identify malware that persists only in memory and is not detected via traditional means. You can use the rich set of contextual information for alert triage, correlation, analysis and pattern extraction.
Threat analytics for admin activity: Security Center can now detect threats targeting your admin activity by analyzing the Azure Resource Management logs. If something abnormal is attempted or permissive privileges have been granted, you will be alerted and can investigate the activity.
Security Center is also extending its threat detection capabilities to PaaS resources. It can now detect threats targeting Azure App Services and provide recommendations to protect your applications.
New partner integrations
Security Center integrates with many partner solutions. We are excited to announce the integration with new partner solutions from Palo Alto and McAfee.
Palo Alto: This integration enables you to streamline provisioning for Palo Alto VM series Next Generation Firewall in the Security Center blade along with integrated threat detection and unified health monitoring of the firewall and simplify deployment.
McAfee: Security Center also supports the discovery and health status reporting of McAfee anti-malware on Windows machines, so you can now receive recommendations from another third-party antimalware service and mitigate potential issues.
Azure Security Center released several new capabilities today that will provide you with better insight, more control, and confidence to keep pace in this ever-changing cybersecurity landscape. Learn how one of our customers, Icertis, achieved better security and gained more productivity by saving 30 percent of operations time by using Azure Security Center.
Start using Azure Security Center’s new capabilities today
The following capabilities are available generally today: integration with virtual machine experience, Web Security Configuration Assessments, and Just-in-Time VM Access.
The following features are available in public preview: Visibility into identity and access controls, File Integrity Monitoring (FIM), Adaptive Application Controls, integration with Windows Defender Advanced Threat Protection, Fileless Attack Detection, and detecting threats targeting Azure App Service and Azure Resource Management logs.
We are offering a limited public preview for some capabilities like the new Security Center dashboard, interactive network topology and security assessments for containers. Please contact us to participate in this early preview.
Learn more about Azure Security Center
Watch our new Azure Friday video to understand the fundamentals of Azure Security Center.
If you are attending RSA 2018 in San Francisco this week, we would love to connect with you at our booth 3501. You can also attend theater session on Azure Security Center on Wednesday, April 18, 2018 at 1:30 PM Pacific Time.
To learn more about how you can implement these Security Center capabilities, visit our documentation.
Source: Azure Blog Feed