Enhancing Threat Protection capabilities and Conditional Access App Controls in Microsoft Cloud App Security
With a growing adoption of SaaS apps to support business processes, it is key to ensure secure handling of data to protect your most valuable corporate assets. With Microsoft Cloud App Security, we are enabling customers to gain insight into and better control of their eco-system of SaaS apps, of and beyond native Microsoft applications.
Today we want to share details around:
- Two new detection capabilities that we are beginning to roll out – Ransomware activity and Terminated-user activity
- The Public Preview of custom activities for deeper visibility and control of user actions via Conditional Access App Control
Enhancing Threat Protection Capabilities
Earlier this year, we announced new threat detection capabilities in Cloud App Security, that included multiple new use-case driven detections, as well as a user-centric investigation experience.
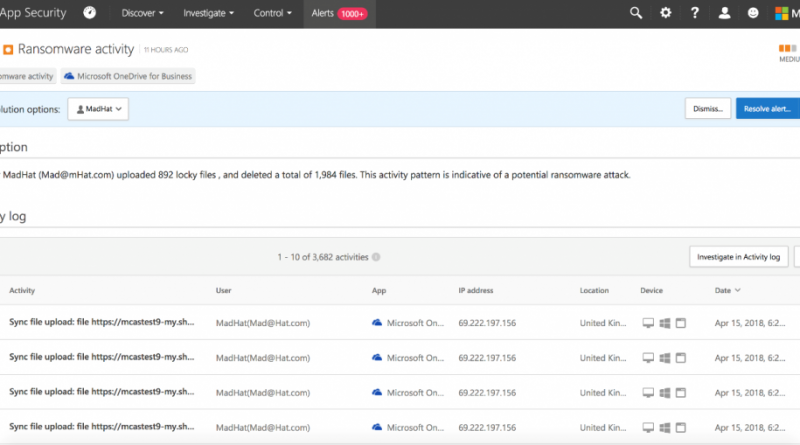
Detecting Ransomware activity
Ransomware attacks remain a common attack vector that both nation-state attackers and financial cybercriminals are leveraging. Recent examples include NotPetya and BadRabbit – both large-scale, nation-state led campaigns, targeting enterprises.
Cloud App Security can already detect Ransomware attacks in a deterministic approach (via activity policy templates), and today were extending this capability with anomaly detection to ensure a more comprehensive coverage against sophisticated Ransomware attacks.
To detect ransomware attacks, we apply our security research expertise in Cloud App Security to identify behavioral patterns that reflect ransomware activity. For example, a high rate of file uploads or file deletion activities can represent an adverse encryption process. This data is collected iin the logs that we receive from the apps API, we then combine these behavioral patterns with Threat Intelligence capabilities, such as the detection of known Ransomware extensions. This interplay ensures that the detection is holistic and robust and will result in relevant alerts within the Cloud App Security alerts dashboard.

Figure 1. Ransomware activity alert – details view
Terminated-user activity
When looking at what can turn a former employee into an insider threat we often see that employees who left their company on bad terms pose the greatest risk. Were seeing that as employees exit a company and their user accounts are de-provisioned from corporate apps as a result, in many cases they still retain access to some corporate resources. This becomes even more important when considering privileged accounts, as the potential damage a former admin can do is distinctly greater.
With the new detection capabilities were introducing today, Cloud App Security (CAS) will be able to identify when a terminated employee continues to perform actions on your SaaS apps. This detection is possible due to CASs ability to monitor user behavior across apps, while user accounts are active. This allows us to profile the regular activity of the user, identify when the account is terminated, and determine activity on other apps beyond the suspension of credentials. For example, if an employee AAD account was terminated, but he or she continues to access the corporate AWS infrastructure, an alert will be triggered.
Public Preview: Define custom activities for deeper visibility and control of user actions via Conditional Access App Control
In November 2017, we announced the public preview of Conditional Access App Control, a feature that works hand-in-hand with Azure Active Directory conditional access, to provide real-time visibility and control of risky user sessions – for example, sessions with external users or users coming from an unmanaged device.
Today, we are excited to share the public preview of new and enhanced capabilities of this feature that facilitate deeper visibility into, and control of various applications. You can now create a Session Policy with an Activity type filter, to monitor and/or block a variety of granular, app-specific activities, such as those shown below. This new filter augments the existing file download control features, to provide you with comprehensive control of the applications in your organization.

Figure 2. Session Policy with various Activity types
When these policies are applied, and end-users come from a risky session, they will be monitored and/or blocked from performing the actions you have selected.

Figure 3. Block notification screen of a user when trying to perform a regulated activity
Marrying these new app-specific actions with the powerful download controls already available provides you with the deep level of control needed to keep your organization secure.
Learn more
Read more about our enhanced capabilities to detect Ransomware and Terminated-user activities here and how you can configure custom activities via Conditional Access App Control. Both will be gradually rolled out to all tenants.
If you have Microsoft Cloud App Security deployed, you will soon start seeing these features in your tenant. If not, you can try Microsoft Cloud App Security for 90-days with no additional cost and see how this service helps you with providing visibility, data control and threat protection to your cloud apps.
We love hearing your feedback. Get started today, give these new features a try and let us know what you think in the Microsoft Cloud App Security Tech Community.
Source: EM+S Blog Feed