Monitor your ADFS sign-in activity using Azure AD Connect Health’s risky IP reports
Howdy folks!
Many of our customers use Active Directory Federation Services (ADFS) to sign into Office 365 and other cloud and on-premises apps secured by Azure AD. ADFS proxy servers are often deployed to enable users to sign in from outside the corporate network.
In a previous blog post, we talked about the kinds of attacks that hit this internet-facing infrastructure and ways to secure your ADFS infrastructure and Azure AD sign-ins. One of the keys to protecting your organization from these kinds of attacks is to assure you can monitor and audit what’s happening with your on-premises identity infrastructure.
To help improve your ability to monitor and audit you identity infrastructure, today we’re releasing a public preview of a really useful improvement to Azure AD Connect Health, Risky IP Reports. This new capability will equip you to better defend against extranet attacks. Risky IP Reports let’s you:
- Easily detect risky external IP addresses that are generating large numbers of failed logins
- Get instant email notifications when risky IP address are detected
- Download detailed reports to perform offline analysis or share within your organization
- Customize your threshold settings to match the security policy of your organization
Before we get started, you’ll need to install Connect Health for ADFS to get this cool new feature. It’s super simple and should take you less than 30 minutes to get started!
Introducing the Risky IP report
When ADFS processes a sign-in request, it audits both successful and failed authentication attempts to the event log. The Azure AD Connect Health service monitors this sign-in activity on your ADFS servers and analyzes it in the cloud. Sign-ins on your ADFS servers are aggregated by IP address and consolidated across the servers in your ADFS farm. Azure AD Connect Health generates an alert when an IP address crosses a threshold of failed logins (hourly or daily).
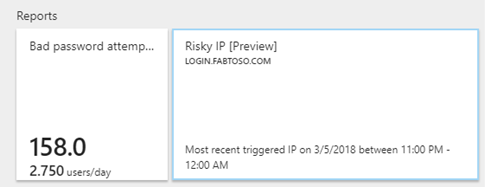
In the Azure AD Connect Health dashboard for your ADFS farm, you will notice a new tile called ‘Risky IP’, which you can click to view the report.

Below is a sample risky IP report that illustrates risky sign-in activity aggregated by IP address. In the report you can see the number of bad password errors and ADFS extranet lockout errors from a given IP address, along with the number of unique user accounts involved in the authentication attempts. Extranet lockout error counts will only show up when your ADFS servers are configured for the extranet lockout feature. We strongly recommend enabling this feature if you allow logins from the internet with password authentication.

You can use this report to identify risky IP addresses that are trying to attack your ADFS authentication endpoints and take the necessary steps to block them from accessing your ADFS servers. You can also use the Azure AD Connect Health Bad password attempts report to correlate and identify affected user accounts, and then encourage those users to change their passwords and pick stronger passwords.
The risky IP report helps you detect password spray or password brute force attacks quickly and without the effort involved in correlating logs across multiple ADFS servers. Read more about ADFS extranet lockout and details in the Risky IP report.
You can also download a report that provides information about all external IP addresses enacting failed logins. This is useful for offline analysis or establishing baselines for your organization. The report includes IP addresses that haven’t triggered any alerts and is useful to detect additional threat patterns.
Note: To get this report, make sure your ADFS auditing is enabled.
Customize threshold settings for alerting
Connect Health generates alerts when an IP address crosses an hourly or daily threshold. With our private preview we got strong feedback letting us know that our customers have a wide range of security policies and would need customizable threshold settings. So we gave you just that! This is easy to configure and has baseline defaults set by us.

We have an FAQ section covering a few common questions customers asked us during private preview.
Summary
If you’re using ADFS for authentication, we strongly recommend you install Connect Health for ADFS and use this report to monitor for password attacks. We’ll also be releasing additional capabilities in ADFS and Connect Health for ADFS in the coming months to help your organization continue protecting your users. Stay tuned for more announcements!
We’re always looking for feedback from you! If you have feedback or feature requests related to this new capability, please let us know in the Connect Health section of ourfeedback forum or feel free to email us.
Best regards,
Alex Simons (Twitter: @Alex_A_Simons)
Director of Program Management
Microsoft Identity Division
Source: EM+S Blog Feed