Introducing the Azure Terraform Resource Provider
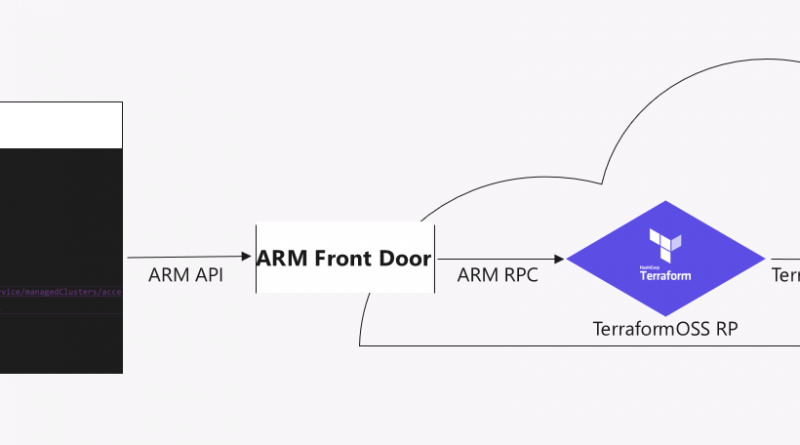
We are pleased to announce a private preview of a new Azure Resource Provider for HashiCorp Terraform which will enable Azure customers using Azure Resource Manager (ARM) to provision and configure dependent resources with Terraform Providers as if they were native Azure Resource Providers.
We have been investing heavily in Terraform and partnering closely with HashiCorp on enabling deep and rich support of Azure for customers who use Terraform to manage their resources. This new capability seeks to enable customers who choose to use ARM directly to enjoy the benefits of Terraform’s broad and diverse set of providers directly through Azure.
There are many scenarios that will be enabled by this new Azure Resource Provider (RP). For example, a customer can now write an ARM template that creates a new Kubernetes Cluster on Azure Container Service (AKS) and then, via the Terraform OSS provider, Kubernetes resources such as pods, services, and secrets can be created as dependant resources.
Provision 3rd party resources inside or outside of Azure using ARM APIs using Terraform RP.
Using the Resource Provider
The provider exposes two types:
- providerregistrations
- resources
Providerregistrations Type
The providerregistrations type correlates to the provider type in Terraform and contains connection and authentication information.
In the example below, a new providerregistration is created, in the properties of the resource the providertype property is set to kubernetes, this instructs the RP to use the Terraform Kubernetes Provider, in the settings object we set the inline_config property of the provider to the credentials (kubeconfig) for a pre-existing AKS managed Kubernetes cluster. The credentials are obtained by calling the ListCredential action on the AKS resource.
{
"type": "Microsoft.TerraformOSS/providerregistrations",
"name": "[parameters('resourceName')]",
"apiVersion": "2018-05-01",
"location": "northeurope",
"properties": {
"providertype": "kubernetes",
"settings":
{
"inline_config": "[Base64ToString(ListCredential(resourceId('Microsoft.ContainerService/managedClusters/accessProfiles', parameters('resourceName'),'clusterAdmin'), '2017-08-31').properties.kubeConfig)]"
}
}
}
Resources Type
The resources type maps onto a resource type in Terraform. In the resources example below a new resources type is defined to create a pod on a Kubernetes cluster, its resourcetype property is set to kubernetes_pod which instructs the RP to use the Terraform kubernetes_pod resource, the resource is bound to a specific kubernetes cluster by setting the providerId property to the resourceId of the previously created providerregistrations type. The settings property schema maps directly to the arguments accepted by the kubernetes_pod resource in Terraform.
{
"type": "Microsoft.TerraformOSS/resources",
"name": "NginxPod",
"apiVersion": "2018-05-01",
"location": "northeurope",
"properties": {
"providerId": "[resourceId('Microsoft.TerraformOSS/providerregistrations', parameters('resourceName'))]",
"resourcetype": "kubernetes_pod",
"settings": {
"metadata": [
{
"name": "nginx",
"labels": {
"App": "nginx"
}
}
],
"spec": [
{
"container": {
"image": "nginx:1.7.8",
"name": "nginx",
"port": {
"container_port": 80
}
}
}
]
}
},
"dependsOn": [
"[resourceId('Microsoft.TerraformOSS/providerregistrations', parameters('resourceName'))]"
]
}
Both of these types have been modelled as top-level resources in the Resource Provider, this means it is possible to use Azure Role Based Access Control (RBAC) to secure the provider information so that people who need to manage resources in that provider do not need to have access to credentials and connection information. In addition, it also makes it possible to have a single set of resource templates that are usable across multiple environments simply by changing the resource reference to the providerregistration. Azure Policy can also be applied to govern the use of this new Resource Provider.
Terraform Providers supported in the initial private preview release
In the initial private preview release we have support for three providers:
As we move from private preview to public preview to GA, we will add support for additional providers. Our intention is to support as many of the Terraform providers as is viable (excluding other cloud platforms). Once released we expect that as new providers are added to Terraform we will work to also enable them in Azure.
How to participate in the private preview
If you are interested in getting access to the private preview, please complete this Azure TerraformOSS Resource Provider Private Preview questionnaire.
Source: Azure Blog Feed