Managing risky 3rd party app permissions with Microsoft’s CASB
While the focus on cloud-based services continues to drive modern IT, the cloud is also making it increasingly easy for users to source new cloud applications without IT oversight in their quest for productivity. In most cases this leads to an increase in cloud-based Shadow IT across Software as a Service (SaaS) solutions, Infrastructure as a Service (IaaS), as well as connected 3rd party applications, and exposes organizations to new threats.
In this post we will discuss 3rd party app permissions as a specific form of Shadow IT and the threat vector that is created when these are authorized against sanctioned IT applications, using protocols such as Open Authentication (OAuth). Furthermore, we will review recent attacks and outline how Microsoft’s Cloud Access Security Broker (CASB) capabilities can help you gain insights into this specific form of Shadow IT and how to safely adopt OAuth apps in your environment – allowing you to balance security and user productivity.
Understanding OAuth
OAuth is a web-based industry standard protocol that enables users to grant web applications access to their accounts and data without sharing their credentials and was originally created for consumer-focused services such as Facebook or Twitter. More recently, the enterprise adoption of OAuth is increasing as a result of the continued adoption of cloud-based solutions in corporate environments, as it allows to simplify login processes across the numerous cloud applications in use.
Once a user authorizes an app, an access token is created and provides the application with programmatic access to the user’s corporate data. This process allows the application to take advantage of the assigned permissions until the token is manually revoked. Contrary to common perception, a change in the user’s password or introducing a second factor for authentication afterwards, will have no effect on the app’s access token.
Based on data from Microsoft Cloud App Security, we’re seeing a continued increase in the number of authorized 3rd party apps. While on average organizations, regardless of size, have 81 authorized OAuth apps in their environment, some organizations already have more than 250 apps.
OAuth apps as a threat vector
While extremely convenient, OAuth introduces a new threat vector to the security of organizations and enables potential back doors into corporate environments when malicious apps are authorized. OAuth was introduced as a more recent form of phishing techniques, where attackers trick users into granting access to rogue applications. Stats show that 4% of people will click on any given phishing campaign[1] with the cost averaging at $1.6 million when an organization is affected by a phishing campaign.[2]
OAuth phishing specifically exploits the users’ inability to differentiate legitimate from rogue cloud applications. One of the most prominent attacks by the hacker group Fancy Bear in 2017, was designed to impersonate the Gmail interface and thereby steal user’s access token and gain access to their accounts.
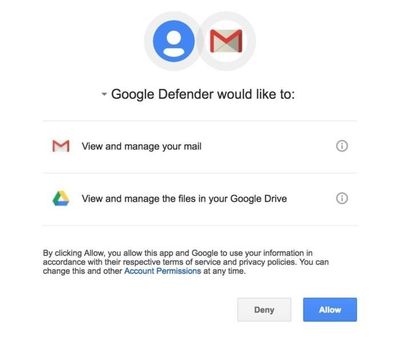
In this scenario, attackers rebuild web pages to make them look nearly identical to genuine web page that users will believe they are accessing. Unless users closely inspect the web address, they may not realize that they are instead providing permissions to a rogue web application.
Unfortunately, users often click “accept” without closely reviewing the details on the permissions they are granting to individual apps – and the more privileged the user, the higher the risk of exposure. This problem is elevated by the fact that IT may have no or little insight into the apps that have been authorized or lack the tools to evaluate the security risk of an application against the productivity benefit that it provides.
Safely adopting and managing OAuth apps with Microsoft’s CASB
Microsoft Cloud App Security (MCAS) provides a comprehensive solution with reporting and analytics on the use of Shadow IT, as well as deep investigation and remediation capabilities to limit the risk and exposure for organizations.
To address the risk of 3rd party app permission, MCAS enables IT to gain an overview of authorized applications across their cloud services Office 365, Salesforce and GSuite. The capabilities allow them to continuously monitor new app permissions and provides controls to prevent and remediate malicious OAuth apps from gaining access to corporate data.
Managing app permissions
Microsoft Cloud App Security app permissions enable you to see which OAuth applications have access to Office 365, G Suite, and Salesforce data, view a full list of permissions that were granted to the app, and which users granted these apps access.
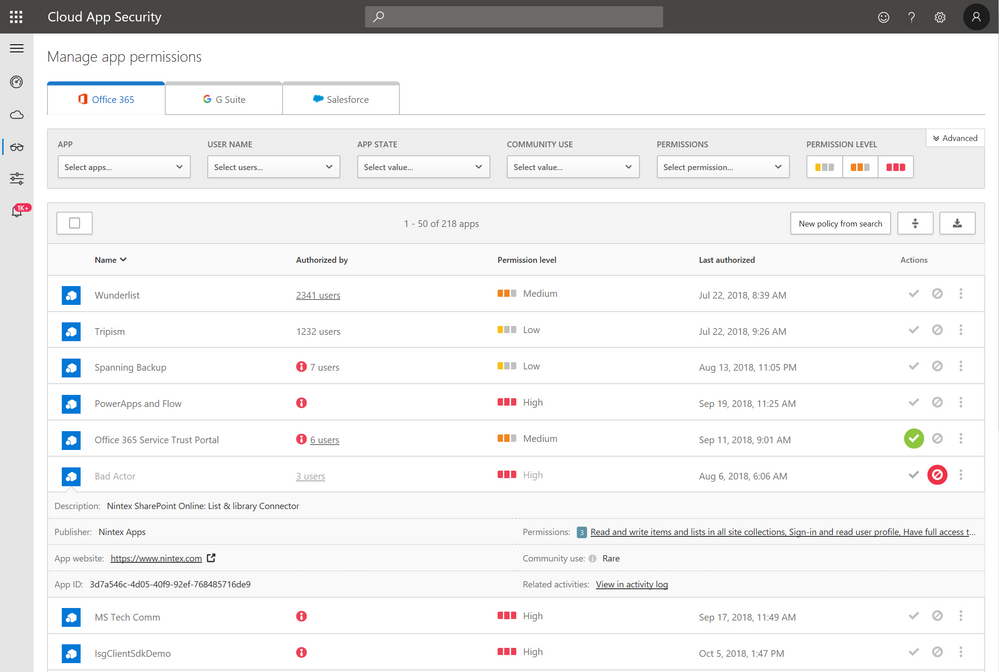
To better understand unknown applications, admins have the ability to drill down into the details for each app and analyze them against their permission levels, the community use- which indicates how common the app is in other organizations- and view related user activities that were logged by MCAS.
Revoking risky apps and notifying users
Community use and the permission level details help admins decide which apps users are allowed to continue to access and which ones will be revoked.
Once reviewed, admins can easily mark an app as approved in the organization, to indicate that it’s been reviewed and approved for organizational use, while apps considered risky can be marked as “banned”, which will revoke the apps permissions.
For continuous monitoring of the OAuth apps connected to your envrionment, you can create permission policies that will notify admins when an OAuth app meets a set of pre-defined criteria. Admins can for example configure to be alerted when new apps that require a high permission level were authorized by a large set of users or privileged user accounts.
To minimize the impact to your organization, these alerts can be configured with governance actions to automatically revoke the permissions of an app that is considered risky.
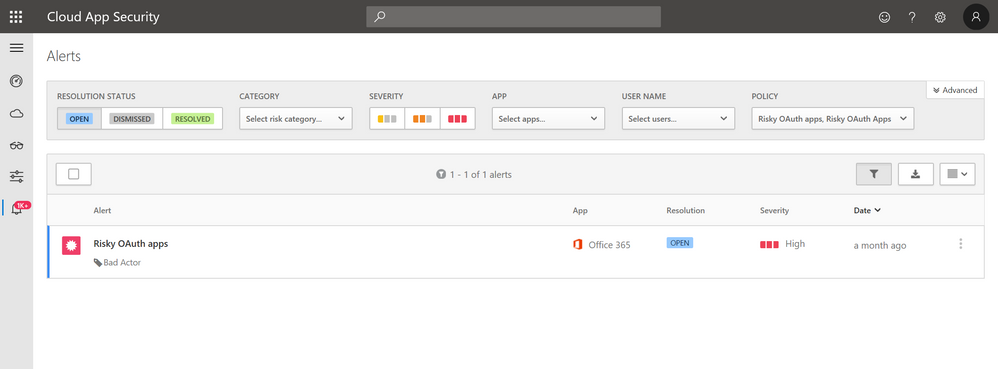
OAuth apps are becoming increasingly popular among end users in corporate environments, as well as attackers, that’s why it’s crucial for organizations to continually monitor authorized apps and identify risky apps quickly to limit the impact to your organization.
More info and feedback
Learn how to start managing your app permissions with Microsoft Cloud App Security using our technical documentation.
Don’t have Microsoft Cloud App Security? Start a free trial today and take a look at our datasheet for an overview of our key use cases and integrations.
As always, we want to hear from you! If you have suggestions, questions, or comments, please let us know on our Tech Community page.
[1] Verizon Data Breach Report, 2018
[2] Enterprise Phishing Resiliency and Defense Report 2017
Source: EM+S Blog Feed
