Discover Shadow IT across IaaS and PaaS with Microsoft’s CASB
Infrastructure-as-a-Service (IaaS) initiated the decline of traditional data center strategies. Today, modern cloud-focused IT strategies enable organizations to implement new processes and scale their infrastructure up and down as needed, allowing them to reach cost efficiencies and high levels of flexibility.
Whether organizations have chosen a single- or multi-cloud vendor strategy, they are often surprised when they find that a business unit has servers on a platform without any IT oversight. PaaS adoption is often driven by developers, as they work on custom applications, or even business-users. When the use of IaaS and PaaS services is driven by these user groups, it often happens without any IT oversight and can go unmonitored for extended periods of time, posing significant security risks to an organization.
Take for instance storage solutions. Microsoft Azure blobs, Amazon Web Services S3 buckets, or Google Cloud Platform storage buckets, can host business-critical resources such as documents, databases, and source code. A simple access misconfiguration can expose sensitive information and lead to malicious exfiltration. Data shows that organizations often have hundreds of custom apps running in the cloud, while our research suggests that only a fraction is managed with IT oversight.
Therefore, it’s important to establish IT oversight from the beginning to avoid stale.
Microsoft Cloud App Security has extended its Shadow IT Discovery capabilities to detect resources that are hosted on IaaS and Platform-as-a-Service (PaaS) solutions across Microsoft Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP), with more being added soon.
The new “Discovered resources” tab in the portal provides you with visibility into the custom apps that run on top of your IaaS and PaaS subscriptions.
You can use this new capability to gain full visibility into the resources that exist within your organization, which users are accessing them, transactions, IP addresses, and how much traffic is being transmitted.
Image 1 shows the new “Discovered resources” view in Microsoft Cloud App Security and the drill down into one of the discovered resources.
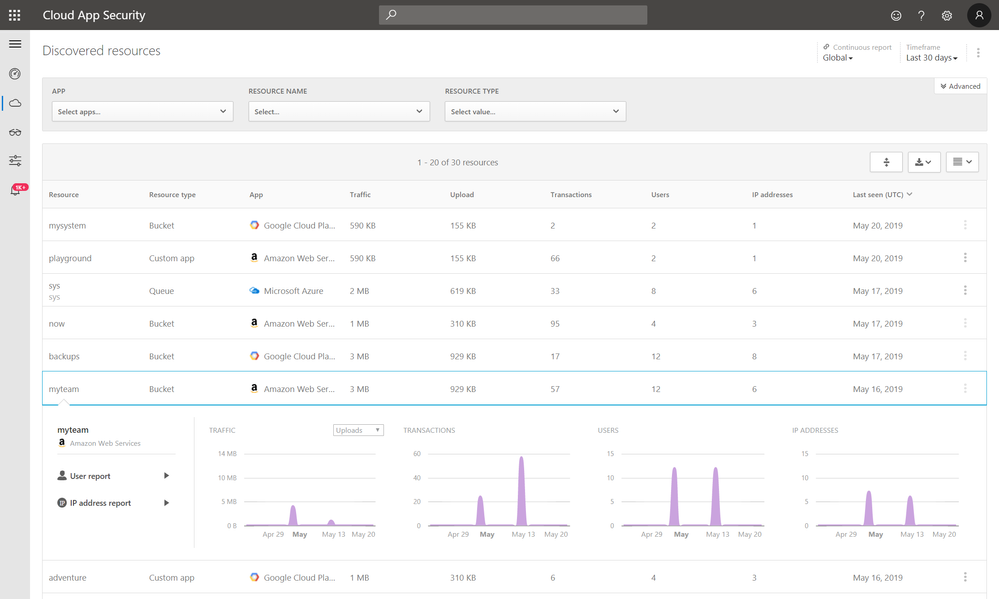
The data is collected based on the same implementation used for the Discovery of SaaS Shadow IT, where customers can choose between Microsoft Defender Advanced Threat Protection for endpoint-based data collection, a log collector or by integrating with their existing Secure Web Gateway.
More info and feedback
Get started with our technical documentation today.
Haven’t tried Microsoft Cloud App Security yet? Start a free trial today.
As always, we want to hear from you! If you have any suggestions, questions, or comments, please visit us on our Tech Community page.
For more resources and information go to our website.
™2019, Amazon Web Services logo is a trademark of Amazon.com, Inc. or its affiliates in the United States and/or other countries.
©2018 Google LLC All rights reserved. Google and the Google logo are registered trademarks of Google LLC.
Source: EM+S Blog Feed
