Creating an Azure NetApp Files Account using Terraform
In this post we are going to talk about using Terraform to create an Azure NetApp Files account in Azure. As well as an Azure NetApp Files account, we will also deploy an Azure Keyvault that will be used for the Active Directory connection username and password. I wrote about creating an Azure Keyvault in a previous post, you can review it here. In this article we are going to be using Terraform to deploy these network resources.
Please note, you must have registered your subscription to use the NetApp Resource Provider. For more information on this please have a look at the docs page here.
Hopefully you’ll have a code editor and Terraform installed on your system. If not, to get them installed, whiz on over to this article here.
What are we building today?
Today we will be building the following resources:
- 1 x Resource Group
- 1 x Keyvault
- 1 x Secret
- 1 x Azure NetApp Files account
The Terraform code used for this lab can be found in my GitHub here. The files in the repo are used to do the following:
- main.tf – Used to specify providers and create the resource groups
- variables.tf – Used to define variables for this deployment. They are defaults and referenced using the terraform.tfvars file.
- terraform.tfvars – This is file the only file you’ll need to edit amend parameters for your deployment.
- output.tf – This file will be used will be used to capture the randomly generated name of the Resource Group for future deployments that need to reference the name of this resource group.
- keyvault.tf – This file will be used to create the Azure Keyvault and Secret. These will be used in future deployments to specify the username and password for Virtual Machines.
- anf_account.tf – This fileis used to create the Azure NetApp Files account.
Let’s build our Keyvault & Azure NetApp Files account
1. We will require a resource group to host our Keyvault and ANF account, this will be built using the main.tf file. The code below will be used to set the Terraform provider and create a resource group in Azure. It will also add resource tags to the resource group.
terraform {
required_providers {
azurerm = {
# Specify what version of the provider we are going to utilise.
source = "hashicorp/azurerm"
version = ">= 2.90.0"
}
random = {
source = "hashicorp/random"
version = "3.1.0"
}
}
}
provider "azurerm" {
features {}
}
# Create random string - This will create a random character string to be used for naming of resources
resource "random_string" "rg_random_1" {
length = 4
special = false
}
# Create Resource Group 1
resource "azurerm_resource_group" "rg_1" {
name = "${var.rg_name_1}-${var.region_1}-${random_string.rg_random_1.result}"
location = var.region_1
tags = {
Environment = var.tag_environment
CreatedBy = var.tag_createdby
CreatedWith = var.tag_createdwith
Project = var.tag_project
}
}2. Next, we are going to deploy an Azure Keyvault & Secret, the keyvault.tf file is used to complete this task. This is purely an example that can be used to randomly generate a password that can be used in the Active Directory configuration. The code below shows how we create the keyvault and set access permissions. It also includes resources tags, remember, always use resource tags!!
# Create Keyvault ID
resource "random_id" "keyvault_name" {
byte_length = "3"
prefix = "keyvault-${var.prefix}-"
}
# Create Keyvault
data "azurerm_client_config" "current" {}
resource "azurerm_key_vault" "keyvault" {
depends_on = [azurerm_resource_group.rg_1]
name = random_id.keyvault_name.hex
location = azurerm_resource_group.rg_1.location
resource_group_name = azurerm_resource_group.rg_1.name
enabled_for_disk_encryption = true
tenant_id = data.azurerm_client_config.current.tenant_id
soft_delete_retention_days = 7
purge_protection_enabled = false
sku_name = "standard"
access_policy {
tenant_id = data.azurerm_client_config.current.tenant_id
object_id = data.azurerm_client_config.current.object_id
key_permissions = [
"get",
]
secret_permissions = [
"get", "backup", "delete", "list", "purge", "recover", "restore", "set",
]
storage_permissions = [
"get",
]
}
tags = {
Environment = var.tag_environment
CreatedBy = var.tag_createdby
CreatedWith = var.tag_createdwith
Project = var.tag_project
}
}
# Create Keyvault Admin Password
resource "random_password" "admin_random_password" {
length = 20
special = true
}
# Create Keyvault Secret
resource "azurerm_key_vault_secret" "admin_secret" {
name = var.labadmin
value = random_password.admin_random_password.result
key_vault_id = azurerm_key_vault.keyvault.id
depends_on = [azurerm_key_vault.keyvault]
}3. Now, we will create the Azure NetApp Files account, as mentioned before, make sure that you have registered for the NetApp resource provider before you try to deploy your ANF account. The code below shows how we create the ANF account. It also includes resources tags, remember, always use resource tags!!
# Create Azure NetApp Files Account 1
resource "azurerm_netapp_account" "anf_acc_1" {
name = "anf-${var.region_1}-${random_string.rg_random_1.result}"
resource_group_name = azurerm_resource_group.rg_1.name
location = var.region_1
# Acitve Directory configuration.
active_directory {
username = azurerm_key_vault_secret.admin_secret.name
password = azurerm_key_vault_secret.admin_secret.value
smb_server_name = var.smb_server
dns_servers = [var.dns_server]
domain = var.domain
organizational_unit = var.ou
}
tags = {
Environment = var.tag_environment
CreatedBy = var.tag_createdby
CreatedWith = var.tag_createdwith
Project = var.tag_project
}
}Deploying the code
Once you have your files in your Terraform directory you can go ahead and deploy the code. To do this, open your editor of choice and browse to your Terraform directory.
1. In your Terraform directory, run the following command to initialise the Terraform deployment and download the required modules.
terraform init2. Next we need to create a Terraform plan. This is used to determine what is required to create the configuration you have specified in your Terraform directory. To do this, run the command below.
terraform plan -out main.tfplan3. Now that you have generated your Terraform deployment plan, we can push the Terraform code into Azure and create our resources. Run the command below to apply your code.
terraform apply main.tfplan4. That’s it, you have now deployed your resource group, keyvault and Azure NetApp FIles account. If you have a look in the Azure portal you will see the resource group you created and within it the resources.
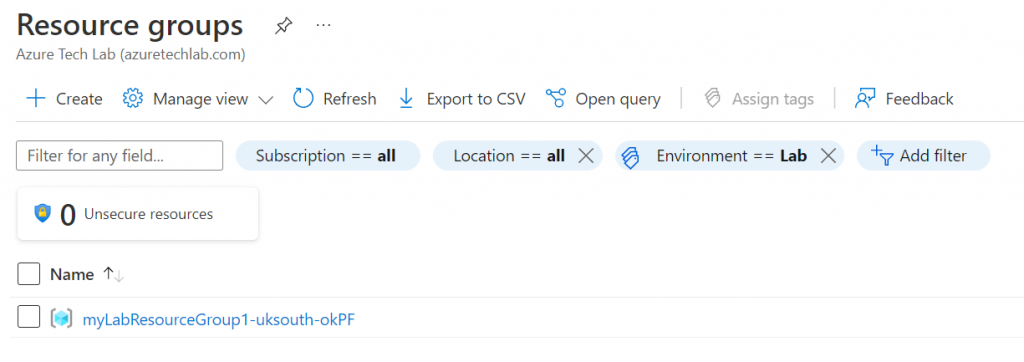
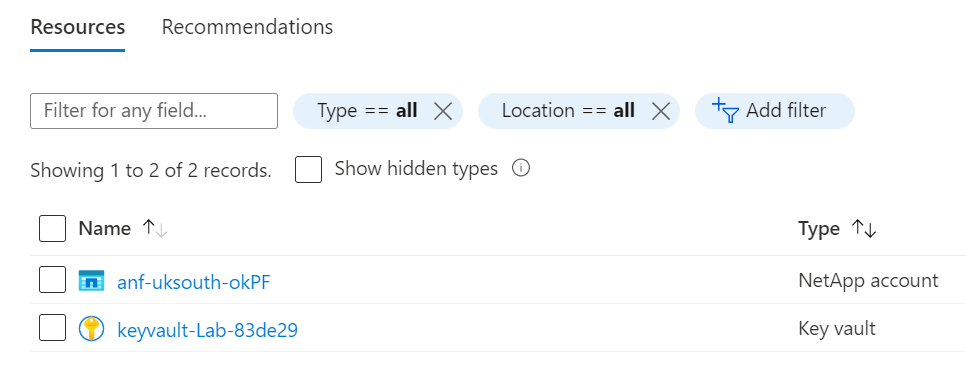
5. Now that you have successfully deployed your resources into Azure, once you have finished with them, it’s time to clean it up and remove your deployment. This is quite straightforward, simply run the command below. This will use the .tfstate file and destroy all resource that terraform built using the apply command previously.
terraform destroySummary
I hope that this very short blog post about creating an Azure NetApp Files account using Terraform has been helpful? I think that the more you use this toolset to deploy infrastructure into Azure, the more you will appreciate its power and simplicity. In my next blog, we’ll build upon this one and add more services into the resource group. Next time, its creating Azure NetApp Files capacity pools 😊