Detecting remote code execution with Microsoft Advanced Threat Analytics
We know that attackers can often use legitimate tools to take malicious actions. Recent incidents have been perpetrated using a known technique called Remote Code Execution (RCE) to spread malware inside a target network. This technique can be executed using legitimate tools such as WMIC and/or PSExec.
Attackers prefer to use RCE instead of Remote Desktop Protocol (RDP) to connect to machines as it gives them stealth access and take control or harvest credentials on remote machines, including Domain Controllers (DC).
Once an attacker can execute arbitrary commands on a DC they dont just have ownership of that DC, but they control the entire Active Directory Forest. RCE remains a significant threat which allows an attacker to run arbitrary code on the destination machine.
However, what attackers may not know is that this technique can be detected with Microsoft Advanced Threat Analytics (ATA). Historically, ATA has been able to detect RCE with PsExec. In version ATA 1.8, the RCE detection capability was extended to include the Windows Management Instrumentation (WMI). Having this visibility of remote execution on DCs is a critical detection trigger to start an investigation.

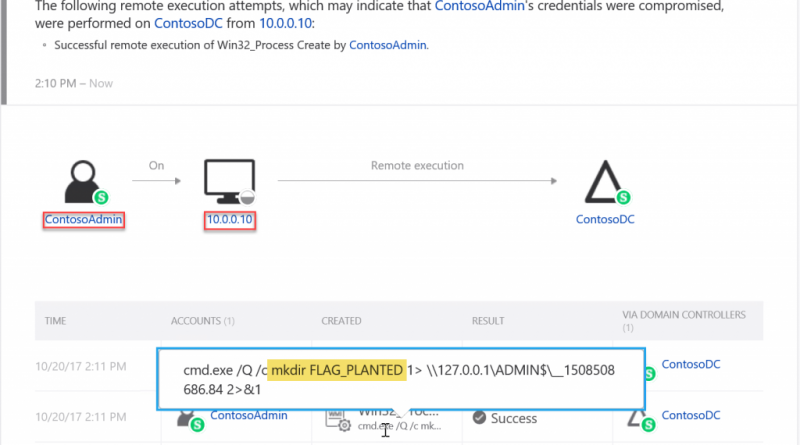
In the screenshot we see ATA has detected an RCE attempt leveraging the ContosoAdmin account, which executed the command, the source computer (10.0.0.10; our Kali machine) and the WMI command passed (mkdir FLAG_PLANTED). This information is very valuable for starting the investigation.
Want to test out ATA? Get a 90-day evaluation copy.
Have a question? Ask your questions and join the discussion with our team on theMicrosoft Advanced Threat Analytics Tech Community site!
All the best,
Hayden Hainsworth (Twitter: @cyberhayden)
Customer & Partner Experience Program Leader, Cybersecurity Engineering
Microsoft Cloud + Enterprise Division
Source: EM+S Blog Feed