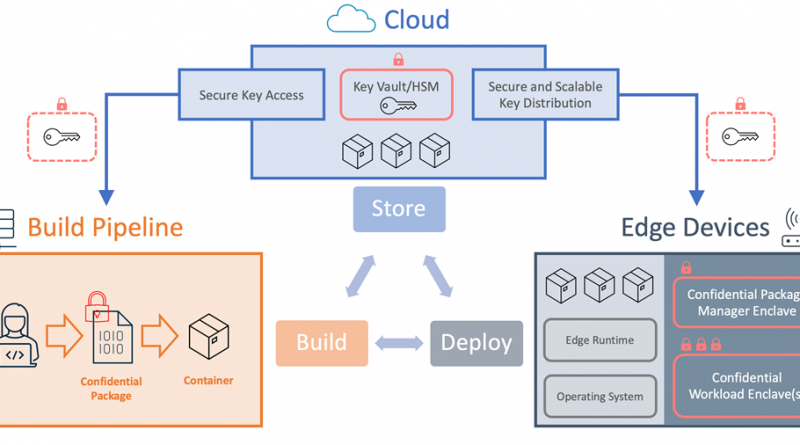
The Enclave Device Blueprint for confidential computing at the edge
A major milestone towards making confidential computing in IoT mainstream for privacy and safety.
In collaboration with Arm® Technologies and Scalys BV, we are announcing the immediate availability of the Enclave Device Blueprint to help towards making confidential computing a mainstream computing paradigm at the edge. The exponential growth in intelligent processing at the edge and autonomous command and control in the internet of things (IoT) necessitates confidential computing to protect privacy and safety. Confidential computing at the edge demands the use of security-hardened and tamper-resistant computing isolations called Trusted Execution Environments (TEE) or simply enclaves. Enclave devices are extremely complex to engineer and operate, and their absence is holding back the fullest potential in edge computing. The Enclave Device Blueprint is here to help simplify the engineering of enclave devices and deploying confidential applications in IoT.
Figure 1: Enclave Device Blueprint Architecture
The rising need for confidential computing
Confidential computing augments traditional computing paradigms with additional protections for computing workloads and data when in use. Traditional computing applies cryptography to encrypt content in the form of computing workloads, data, and AI models when in storage or in transit but must decrypt said content in memory when in use. This model continues to work reasonably well when operating air-gapped compute networks where there are lower concerns for data exfiltration or malicious tampering. IoT and cloud computing, on the other hand, ushers the age of computing characterized by hyperconnectivity, multitenant compute infrastructures, and data-driven autonomous command and control of many systems including critical infrastructure thereby calling for a higher bar for privacy and safety. Confidential computing using TEE offers compute isolations necessary to help deliver on both privacy and safety to help unleash the full power of digital transformations with IoT.
Special considerations for IoT
A major difference to observe in confidential computing in the cloud and at the edge is that while cloud solution providers set up and operate the requisite infrastructure in the cloud for their customers, IoT solution builders are responsible for coming up with enclave devices and the complexity in doing so holds them back.
In addition, while the infrastructure for confidential computing in the cloud resides in datacenters where they benefit from additional facility and operational security controls, IoT and enclave devices are generally deemed to be under constant threat of malicious physical access. To minimize this threat, enclave devices tend to favor binding trust directly or very close to the root of trust hardware (bare metal) over the use of supervisory software like hypervisors and container runtimes to keep the Trusted Computing Base (TCB) at a minimum. Supervisory software on the other hand help abstract from the hardware to enable scale across hardware technologies at a cost of a larger TCB. Having to avoid the scale advantages of supervisory software for higher security is one source of complexity in building, operating, and maintaining enclave devices.
The Enclave Device Blueprint at its core seeks to solve these challenges in a manner that still upholds security at the highest levels possible.
The Enclave Device Blueprint
The Enclave Device Blueprint comprises projects, resources, and guidance to abstract and simplify the development of enclave devices and facilitate the deployment of confidential applications at scale for IoT. It strives to complement traditional computing by filling in the architectural and component gaps towards making confidential computing mainstream in IoT.
The blueprint is agnostic of hardware technologies, operating systems, or solution cloud. It invites a community approach to solve a very complex problem where participants can mitigate cost through collaboration and foster higher security through the transparency that comes with open source. All blueprint components are currently in open source and were developed with the vision for complete community ownership and governance.
A real-world realization
More than just a collection of projects, resources, and guidance, we made sure to validate the efficacy of the Enclave Device Blueprint with a real-world device and project. The Enclave Device Blueprint was inspired by the real observation of the roadblocks holding back confidential computing at the edge. It was, therefore, important to ensure the blueprint address obstacles from real experiences and is backed by real product truth.
While in collaboration for the development of the Enclave Device Blueprint, Original Device Manufacturer (OEM) and secured devices builder, Scalys BV, in tandem engineered TrustBox Edge 201 from the blueprint to satisfy both Azure IoT Edge certified and tamper-resistant enclave device requirements for confidential computing in IoT.
Figure 2: TrustBox Edge 201 (Source: Scalys 2021)
Building on Azure cloud and making use of fully managed services like Azure IoT Edge, Azure IoT Hub, Azure Functions, and Azure Key Vault, we incorporated the software components of the Enclave Device Blueprint to orchestrate an end-to-end at scale build-deploy pipeline for confidential applications in IoT. It is the modular nature of the Enclave Device Blueprint components that make it agnostic to technology, operating system, or the cloud. The full project is available on Azure Samples and ready to try out using TrustBox Edge 201 from Scalys BV. The Enclave Device Blueprint whitepaper provides a detailed explanation for the blueprint components.
The journey continues
The Enclave Device Blueprint delivers a major milestone aimed at spurring the creation of enclave devices and deploying confidential applications at scale in IoT. Enclave devices help provide privacy and safety protections necessary for IoT to unleash its fullest potential. Based on history, one can safely assume that this is only one of many milestones, the most obvious next being seamless integrations with confidential computing services in the cloud for uniform and pervasive cloud-edge confidential computing experiences.
Learn more
- Read the Enclave Device Blueprint whitepaper.
- Get information on how to obtain a Scalys TrustBox Edge 201.
- Visit and experience the project on Azure Samples.
Source: Azure Blog Feed